Two researchers have come up with a new method of hacking smartphones that use fingerprint biometrics to protect and lock the user's data.
Kai Cao and Anil K. Jain from the Department of Computer Science and Engineering at Michigan State University have devised a simpler and faster method of spoofing fingerprints, which can be carried out in 15 minutes or less.
The two are saying that their attack is much more efficient than the one that Germany's Chaos Computer Club (C3) came up with when the iPhone 5S was launched, which involves a 2.5D printed gummy finger made from the author's fingerprint.
The attacker's entire gear can cost less than $500
In their version of the attack, they only used a regular inkjet printer, three AgIC silver conductive ink cartridges, a normal black ink cartridge, and special AgIC paper.
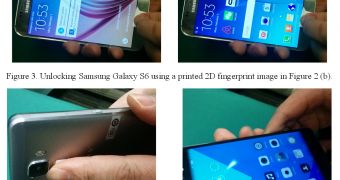
The researchers say that anyone can lift a smartphone's owner fingerprint, even from the stolen phone itself, scan it at 300 dpi, flip it horizontally, and then print it on the glossy side of the special AgIC paper.
They can then cut out the fingerprint, place it over the phone's fingerprint scanning sensor (whichever that may be, depending on brand), and the phone will recognize it and grant access to the data to the attacker.
Samsung and Huawei phones already hacked
All of this takes around 15 minutes to carry out and was successfully tested in a laboratory against a Samsung Galaxy S6 and a Huawei Honor 7. The researchers said that while the Samsung was easy to crack, the Huawei phone needed more tries.
With fingerprints and biometrics in general poised to become the next big thing in online security, the report shows how unsafe this authentication system really is for today's tech environment.
For more details, please consult the Hacking Mobile Phones Using 2D Printed Fingerprints research paper. Below is a video of the attack.
 14 DAY TRIAL //
14 DAY TRIAL // 